Tracking Cookie
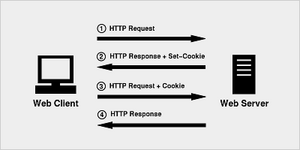
A tracking cookie (also called a HTTP Cookie or sometimes simply cookie) is a small web file that is downloaded to a user's computer when using websites that utilize cookies. Tracking cookies were initially designed to be a reliable method of storing important information about a user. Cookies are used to store information such as items in a shopping cart when a user leaves the website and later comes back to it, some of the other uses include recording browsing activity (logging activity, and sometimes recording pages that were visited in the past), lastly the most volatile usage of a cookie by a user is the auto-fill feature where a cookie automatically fills in certain pieces of information that were previously recorded.
Structure of a Cookie
A cookie consists of 3 components.
1.) Name- is the official name given to the cookie by its creator.
2.) Value- value determines which type of cookie it is.
3.) Attributes- Attributes determine the power of a cookie with things such as expiration, domain, and its security level.
Types of Cookies
Session Cookie
A session cookie exists only in the RAM and is deleted after the user closes the Internet Browser. It is used to remember short term information like website last visited.
Secure Cookie
A secure cookie is a type of cookie that has been verified as secure due to it being transmitted over the encrypted connection known as HTTPS.
Third-party Cookie
A third-party cookie is a type of cookie that is mostly used for advertising purposes. While visiting a website it will download a specific cookie associated with that website and will show information relating to the website it came from. Third-party cookie means that the cookie belongs to a different domain but can show itself on other websites mostly through advertisements.
Zombie Cookie
A zombie cookie is a type of cookie that can automatically recreate itself after the user has deleted it. Zombie cookies are not allowed by certain browsers and are viewed as unethical when companies use them.
In 2017, Alphabet (Google) was ordered to pay $5.5 million due to their usage of zombie cookies on specific web browsers that do not allow it.[1]
Uses of Cookies
Management
The original purpose of a tracking cookie was to save information as a user was navigating through a website (for example; saving items to the shopping cart and as you browse they are still there).
Cookies can also be used to keep a person logged into their account on a website so that they do not have to re-login every single time they want to access the site.
Some concerns exist about session cookies due to them have limitless possibilities in what they can collect about a user.
Tracking
Tracking cookies can be used to track a user's IP address. A cookie can collect a log file of the websites that a user has visited, and even tell you how long the user for on the website for. Many companies analyze the users' web patterns to try and make more applicable products.
Individualization
Cookies are mostly used to remember simple information to create a better web experience. Some examples of simple information remembered, are auto-fill data like websites last used by a user, or username and password on a website that requires you to log in.
Privacy Concerns
Tracking cookies have lots of privacy concerns to such an extent that the government gets involved. There are many laws in the United States that are supposed to limit the usage and vulnerabilities of the United States but it is hard to enforce. [2]
Session Hijack
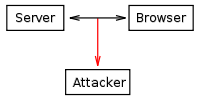
A session hijack cookie is a type of cookie that relies on imitating a real cookie and collecting information from the user. A session hijack cookie can collect information such as usernames and passwords which could lead to your personal information being exposed to hackers.
Network Eavesdropping
A network eavesdropper is a type of cookie that can be attached to an unsecured computer usually over an open WiFi. A hacker could see all of the information that the user is processing and can use that information to impersonate and perform fraud.