New Media Technology
Introduction and General Overview
The intellectual roots of artificial intelligence (AI), and the concept of intelligent machines, may be found in Greek mythology. Ancient and Classical philosophers describe the process of human thinking as the mechanical manipulation of symbols. The term “artificial intelligence” itself was first coined by John McCarthy in 1955 in the Dartmouth Conference; the first conference devoted to the subject. McCarthy defines AI as "the science and engineering of making intelligent machines”.[1] AI began with an ambitious research agenda; the main purpose is to present machines with some humanly traits that we value most in ourselves. As rational beings, we humans tried to create machines that think and act like us. You can also say intelligence is based on rationality: acting humanly, thinking cognitively and behaving rationally. These all factors includes reasoning; skill in solving problems, creativity, the capacity to learn from experience.[2] Using these principles AI has overtaken almost all aspects of our everyday lives and is helping people in every field make better use of information to work smarter, not harder. However, AI still is a miracle created by human mind. No matter how easy and sufficient these technologies are for our lives; they are all still operated and constructed by the sharpest human minds which cannot be substituted by any artificial intelligence. Natural intelligence itself is developed and nurtured over the years with experience. Artificial Intelligene, however; lacks the emotional and sentimental component of human intelligence.
Artificial intelligence has reached the point now where it can provide invaluable assistance in speeding up tasks such as searching algorithms and enhance technical systems. For example all the social media sites are being operated by AI for the purpose of advertisement and marketing. Gaining useful information from one's Facebook profile or Tweets to suggest friends and use marketing tools to gain attention from the very specific and target audience. The minutes you start shopping at Amazon and accept to receive emails and notifications; your inbox fill with all interesting and related products based on your interest. All is done through AI, which is collecting every nanosecond we spend online and then used for specific interest of different industries.
How Intellectual Machines Can Assist People
Intelligent machines (IM) are created with the thought of having autonomous objects help the humans with their lives. What makes IM so special is the fact that they can think in ways similar to how a human can. This trait allows IM to function without human intervention and solve problems on their own. Computers, by themselves, are not actually considered to be IM. It is the many applications and processes that they can run that qualifies them as IM. Computer applications have AI that utilize complex algorithms to solve problems and assist people with their tasks. One example of a simple feature that people use is auto-complete, which is the ability for applications to remember previous text entries. An application that uses auto-complete keeps a database of words, which are the words that this application can recognize, and expands it by adding new words used by people. By remembering previous search entries, applications can remember words that users prefer to use and predict what users will type. This is a type of learning for these applications; they recall commonly used words that their users frequently type, predicts the word as the user types it, and then suggests it for their users. This way, users can quickly type words without entering all the letters. Auto-complete is one feature that qualifies machines as IM simply because it shows that applications have the ability to learn from past experiences. The auto-complete feature may seem insignificant, but it is only a small sample of what computer applications are capable of.
IM also come in more complex forms. Autonomous robots are recently being developed as advanced IM. Despite still being in early stages of development, robots are providing assistance without any problems. Warehouses today utilize autonomous robots in place of humans to transport goods. These robots create a route around the warehouse all on their own, without the need of input from a human operator. They also avoid crashing into each other while delivering goods through the use of sensors, which allow them to detect obstructions in their path and stopping on the spot. These robots have advanced AI which allows them to think about how to overcome the different situations they are confronted with.[3] They make the warehouse operate more efficiently in multiple ways. These robots can receive a list of goods from anywhere within the warehouse through wireless signals, which is something human workers may have trouble doing even with wireless communication devices. They also perform better than human workers because they never get tired and can work for hours without stopping. Not only do they perform better than human workers, but they also reduce the workload on the workers; warehouse workers don't have to walk around and gather goods when there are robots doing the job. Autonomous robots also have no emotions and won't break down due to stress, making them more consistent workers than human beings. They will never complain or argue for personal reasons such as higher wages or better working conditions. Basically, autonomous robots are better than human workers in nearly every aspect.
Flaws of Intelligent Machines and Artificial Intelligence
Although IM may seem like they only do good for people, they don't always work as intended. IM and AI can malfunction and stop working properly. This happens when there are errors in the algorithms of the AI, which results in the IM not knowing how to respond to certain scenarios. Some technologies aren't perfected yet, such as voice recognition. There are often times when voice recognition devices fail to properly understand speech. This is because of how intricate the human voice can be. There are many things to take into account when dealing with voice, such as accent, volume, pitch, and resonance. It is seemingly impossible to create a device that can perfectly understand the speech of anybody in the world, especially when there are so many different factors to take into account. Another aspect where IM fails is with facial recognition of twins. Technology has advanced to the point where IM is used in facial recognition in phones for security. It is highly advanced and can differentiate between a picture of a face and an actual one with the IM incorporating field of depth. This can accurately determine a person's face even if the person grows facial hair, changes hairstyles, wears glasses, or puts on facial blemishes. Unfortunately, there is an issue with IM recognizing the differences of identical twins. Although this doesn't pose a big threat because a twin is a family member, IM is still being improved to distinguish the faces of twins. IM will eventually steal jobs away from human workers. It may not be happening on a wide scale today, but it might be the case in the future. There is no reason for companies not to replace workers with IM, especially when they work much more efficiently than human workers. Not only do they work more efficiently, but they also have no personal and emotional feelings. This means that they won't be affected by conditions which normally pains people, such as stress and fatigue. IM will always perform at their best; unlike humans, who have varying amounts of work outputs due to many factors that limit them from always performing at their best. IM can basically do everything humans are capable of, but they will always perform better than humans can hope to. If IM were to become the standard for companies and stores all over the world, human beings will become vastly unneeded in the workplace and unemployment levels will rise.
Looking Into the Future
Having already discussed the advantages and disadvantages of the relationships between humans and intelligent machines, we should consequently move forward and analyze what the future could potentially hold and how IMs can be best improved and enriched to function in the most desirable form. Artificial intelligence, or the developing of such intelligent machines, has been around for quite some time now. Yet, with the rapid and abundant growth of technology as a whole in the present day, AI is a force that should be actively considered. After all, it definitively defines what types and kinds of coding will be used for IMs which in turn will express what IMs will result in – an aid to humankind or a complete substitution. According to futurist Ray Kurzweil, in his book The Singularity is Near: When Humans Transcend Biology [4] , we are currently in a technology hype cycle, or highly active cycle, that will result in a technological singularity by the year 2045. This means that AI, thereby IMs also, will reach a state in which it will be so powerful that it will essentially outweigh the combined intelligence of humans and even become one with humans. Instead of looking into cosmetic operations to improve one’s bodily features, we will instead be considering ways of augmenting our minds and bodies with genetic mutations. Thus, IMs will not only be products of humans but also part of the human identity meaning the open possibility of IMs taking part in the control process that dictates our behaviors.
IBM's Watson is also another example of how artificial intelligence can forever change the future. Watson is a computer system that has the ability to answer questions by using both structured and unstructured content. The information it possess includes dictionaries, newspapers, books, and even databases. The supercomputer was named after IBM's founder, Thomas J. Watson. Watson has the ability to process 500 gigabytes of data per second. In 2011, shortly after development, Watson was put to the test and competed on Jeopardy against previous winners Ken Jennings and Brad Rutter. Watson won first prize and received $1 million. A few years later, in 2013, IBM announced that Watson will begin assisting nurses and doctors in making decisions for lung cancer treatment at Memorial Sloan Kettering Cancer Center. Watson is also always constantly learning.
On the other hand, physicist Paul Davis has another take on the futuristic prospective of IMs. In his work, “When Computers Take Over”, a response to Kurzweil’s book, Davis states that the idea of IMs controlling humans is a bit outlandish. First off, he points to what he calls the ‘exponential- growth fallacy’ Kurzweil uses to construct his basis that IMs will become far greater than us. Davis says, “The key point about exponential growth is that it never lasts. The conditions for runaway expansion are always peculiar and temporary..."[5] Furthermore, Davis also goes forward in saying that, “Technology can harness physical laws but it can’t bend them.” Hence, he is implying that while IMs are indeed quite capable of doing and acting at faster speeds than humans, they are still limited by the bounds of those that programmed them. This is good news for us that are not so keen on the idea of letting machines regulate us as a way of keeping up with the times. All in all, IMs seem to be embedded in our holistic picture of the future. The question here is – is that a good thing or a bad thing? Well that truly seems to be dependent on the programmer. Do we have a Dr. Evil behind the scenes encoding IMs or do we have someone who is genuinely coding as a way of best enhancing our futures? How does he, the latter, make these calls of what is ‘best’ moving forward? Perhaps there is no one right answer as even ethical models cannot settle on one straight application that will be beneficial to all. Utilitarianism would call for the advancement of IMs at the effect that they would be most productive for the greatest number of people while meta-ethics would instead examine the definitions of good and bad in our world and see how IMs would impact society in this sense. Thus, while we can consider the implications of IMs in our futures as human beings, we should also be prepared to adapt to the future with caution. IMs will be part of the picture but remember we, now, are the painters.
Big Data
As both technological innovation and world population continue to grow, so does the amount of data on the WWW. "The amount of data that’s being created and stored on a global level is almost inconceivable, and it just keeps growing" (SAS, 2016). These enormous amounts of data are constantly being stored, analyzed, and calculated. This endless cloud of data has been coined "big data". Analyst Doug Laney defined big data as a combination of the three V's: volume, velocity, variety. The concept of big data is relatively new, it first became a recognizable term in the early 2000's. Since big data sets are so complex and large in volume, traditional data processing applications are insufficient. New technologies that are used to analyze big data include A/B testing, machine learning, business intelligence, cloud computing, tensor-based computing and more. Many believe that analysis of big data has big potential for improving every industry.
Social Engineering In The Context Of Engineering
Social Engineering is the usage of human interaction in hopes of breaching security pass and protocols. There are different variations of Social Engineering ranging from Baiting, Phishing, Spear Phishing, and Pretexting. All of these variation requires an interaction with an individual in order for hackers to obtain precious information or gain money. [6]
Baiting
Baiting is when hackers leave USB drives intentionally at random spots such as coffee shops, bookstore, library, virtually any public space. Once they leave the USB, unsuspecting victims would eventually pick up the drive and insert it into their computer without the knowledge that they are virtually opening the doors for hackers. Once the USB drive is in the computer port, hackers have programmed the USB drive to install a malware that can either lock up a computer or download all the personal information inside the computer and send it off to a server. If the computer is locked, there would be a message prompting users to contact someone and pay them to fix the computer.
Phishing
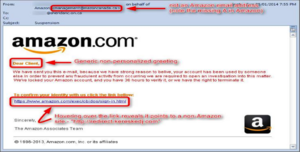
Phishing is the idea of mocking a site and pretending to be a certain site in order to gain the login information of the users that visit the phishing page. Usually these phishing pages are used on bank websites, payment processors, social media and many more sites. Doing stuff online has become an inevitable part of our daily life, most of us have accounts with sensitive information, the risk of doing business online is low as long as we are dealing with websites we trust. Problems occur when hackers/criminals impersonate these organizations, for example, a financial institute, and try to get sensitive information such as bank account and password. They usually make people believe that their account has been illegally accessed and send out a link to fill up a form they ask the account holder to verify his account and password. Once they type their information they’re been scammed. The key to avoiding phishing is awareness.
These are common indicators of phishing attempts: (1) Suspicious sender’s address. The sender's address may imitate a legitimate business. Cybercriminals often use an email address that closely resembles one from a reputable company by altering or omitting a few characters. (2) Generic greetings and signature. Both a generic greeting—such as “Dear Valued Customer” or “Sir/Ma’am”—and a lack of contact information in the signature block are strong indicators of a phishing email. A trusted organization will normally address you by name and provide their contact information. (3) Spoofed hyperlinks and websites. If you hover your cursor over any links in the body of the email, and the links do not match the text that appears when hovering over them, the link may be spoofed. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (e.g., .com vs. .net). Additionally, cybercriminals may use a URL shortening service to hide the true destination of the link. (4) Spelling and layout. Poor grammar and sentence structure, misspellings, and inconsistent formatting are other indicators of a possible phishing attempt. Reputable institutions have dedicated personnel that produce, verify, and proofread customer correspondence. (5) Suspicious attachments. An unsolicited email requesting a user download and open an attachment is a common delivery mechanism for malware. A cybercriminal may use a false sense of urgency or importance to help persuade a user to download or open an attachment without examining it first.
Spear Phishing
Spear Phishing is like normal phishing, but with the twist of it specifically targeting an individual.
Pretexting
Pretexting is when users pretend to be someone else in order to obtain information that they would otherwise not be able to obtain without impersonating someone else.
References
"What Is Big Data and Why It Matters." What Is Big Data? SAS, 2016. Web. 09 May 2016.
- ↑ "History: The Origins of Artificial Intelligence." Association for the Advancement of Artificial Intelligence.N.p., n.d. Web. 05 May 2013. <http://www.aaai.org/home.html>.
- ↑ Hayes, Brian. "The Manifest Destiny of Artificial Intelligence."The Magazine of Sigma Xi, The Scientific Research Society 100 (2012): 282-87. American Scientist, July-Aug. 2012. Web. 5 May 2013.
- ↑ Madrigal, Alexis. “Autonomous Robots Invade Retail Warehouses.” Wired, January 27, 2009, <http://www.wired.com/wiredscience/2009/01/retailrobots/>
- ↑ Kurzweil, The Singularity is Near: When Humans Transcend Biology, Viking/Duckworth, 2005, ISBN 978-0-670-03384-3
- ↑ Davis, “When Computers Take Over”, Nature, p421-422, March 23, 2006.
- ↑ http://searchsecurity.techtarget.com/definition/social-engineering
- ↑ https://www.us-cert.gov/ncas/tips/ST04-014