Security
Security is essentially the safety from all unwarranted harm or change. The main perception of security is that its a form of protection. This includes things such as a lock on a door, to a security guard for a building. However, there are other forms of security such as cyber security, emotional security, secrecy, and assurance.[1] Security, in essence, can be described as a level of freedom against any type of danger
Cyber Security
Cyber Security, or computer security, is the protection of confidentiality, integrity, and availability of computer based systems. This is also known as the CIA Triad.
Confidentiality basically means keeping information secret from unauthorized individuals, entities, or systems. Some of the most common attacks are stealing Personal Identifiable Information (PII), bank and credit card information, trade secrets, and government documents. [1]
Integrity refers to the protection of data and assets from unauthorized and unknowing modifications. When a stream of bits is send across the network it is expected to arrive as the exact same stream of bits at the other end of the transaction. If that's not the case, it means that the data was tampered and there is a loss of integrity. Some of the most common attacks are session hijacking and Man-In-The-Middle (MITM) attack. [2]
Availability is the risk of losing the ability to access your own Information Systems (IS). In this category are included attacks like Denial-of-Service (DoS), Distributed Denial-of-Service (DDoS), and ransomware.
Although the word cyber implies digital/computerized, the defense mechanisms are not only digital. Effective Cybersecurity involves physical aspects as well. The best measures against cyber attacks is having a good combination of both digital and physical controls.
Types Of Cyber Security
Firewall
Firewalls are the most basic first line defense in any computer system. They are used to monitor incoming and outgoing network traffic and helps decide whether to allow or block specific traffic based on a defined set of security rules.[2]
Antivirus
Antivirus programs are types of software specifically designed to protect a computer system against various cyber attacks. Antivirus software looks at all web traffic and programs accessed by the computer system and flags and removes threats. It is important to keep the program updated as there are new methods of cyber attacks being created everyday.[3]
Encryption
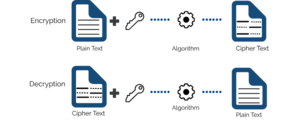
Encryption is essentially scrambling up data in a code. This makes it so that the data is unreadable to anyone who tries to access it. The way to unscramble this is normally with an encryption key. Usually, the person that is encrypting the data will possess the key that locks the data and will make 'copies' and pass them on to relevant people that require access.[4]
Cyber Attacks
Cyber attacks are malicious and deliberate attempts by an individual or organization to breach the information system of another individual or organization. Usually, the attacker seeks some type of benefit from disrupting the victim’s network.[5] Most of these attackers or "hackers" do so for some sort of monetary gain. While the term cyber may be in the definition, many of these cyber attacks happen due to human fallacies. Basically, when a computer system starts to operate less than optimal, there is a high chance the system is under some sort of cyber attack.
Types of Cyber Attacks and Countermausures
Shoulder Surfing
Shoulder surfing is when an attacker looks over a user's screen with the user being unaware and being able to learn sensitive information as a result. This information could be a credit card number, or a login password. Countermasures include avoiding entering of credentials while in crowded places, if in a crowded place, sit with your back to the wall; use of devices that have retina recognition.
Phishing
Phishing is when attackers send fake emails or calls as bait that seem legitimate. The user would fall for this and give up sensitive information. Phishing is normally an attack on an individual user. Larger similar attacks on corporations are called Whaling. Phishing presents the most feared risk in enterprises. Countermeasures include proper inspection of the From and To boxes in the email header; pasting links in the browser; proper configuration of the email client; SPAM filters and using HTTPS connections only.
Denial-of-Service Attack
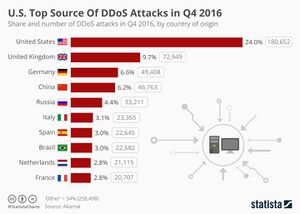
A Denial-of-Service Attack is an attack where the attacker uses multiple computer devices to flood packets into the unsuspecting target's network. The target's network bandwidth gets all used up and can no longer process legitimate requests. These attacks normally target companies to delay or stop their services for various reasons. These attacks are commonly known as DDoS (or Distributed-Denial-of-Service) attacks. Countermeasures include proper configuration of web servers and new-gen firewalls; closing of all unused ports; use of load ballancers.
Malware
Malware is what malicious software is called. This type of software acts like normal software such as an Adobe Flash Player update. Once installed, it can have various effects on your computer.
Types of Malware
Spyware
Spyware is a type of malware that is used to steal information on a computer's hard drive. Once installed, it "spies" on data and sends information from that system to the attacker. An effective countermeasure against spyware is browser configuration not allowing pop-ups, 3rd party cookies, and geotagging; implementing a company spyware protection policy.
Ransomware
Ransomware is a type of malware that holds the computer system hostage. It normally disguises itself as an anti-virus software and won't let you access anything until you pay a fee to "activate" the software. This is the second highest threat after phishing. Effective countermeasures include a scheduled a regular back-up of company data and continuous monitoring of processes. Unlike most malware ransomware is slow and puts a heavy burden on the system performance which make it easier to detect.
Keylogger
A Keylogger is a type of malware that essentially logs the keys a user types. This type of malware essentially can record a user typing a password, social security number, or credit card information and sends it back to the attacker. Countermeasures include monitoring for egress traffic and use of password manager applications.
Botnet
A Botnet is when the attack completely hijacks the computer system and turns it into a "bot". The bot then becomes connected to other hijacked systems forming a network of stolen systems that can be used to distribute all types of malware. This attack has two aspects. First is making sure that your device has not been turned to a bot. An effective countermeasure for that is routinely running the current file system table against a databases of hashes from our previous table. If there is a hash that doesn't match most likely there is an executable that has found its place there without authorization. The second aspect of botnet attack is when it is actually directed towards us. In other words this is just a type of DDoS attack for which we mentioned countermeasures already.
Security Apps
Crowdstrike
CrowdStrike is a SaaS (software as a service) solution that leverages advanced EDR (endpoint detection and response) applications and techniques to provide an industry-leading NGAV (next generation anti-virus) offering powered by machine learning to ensure breaches are stopped before they occur. This guide will give a brief description on the functions and features of CrowdStrike [6]
How does CrowdStrike work? CrowdStrike is an agent-based sensor that can be installed on Windows, Mac, or Linux operating systems for desktop or server platforms. These platforms rely on a cloud-hosted SaaS Solution, to manage policies, control reporting data, manage and respond to threats. [7]. It is a EDR (Endpoint Detection and Response) software that should be in the box of every IT Security professional.
CrowdStrike Falcon Sensors communicate directly to the cloud via two primary URLs. These URLs are leveraged for agent updates, data sync, and threat uploads. These two URLs are:
- ts01-b.cloudsink.net
- lfodown01-b.cloudsink.net
There are not too many places I would not recommend CrowdStrike. I personally use it at work, although very advanced it is user friendly. One of the outstanding features is it intersects with new media. You can configure alerts and customized reports to be sent directly to your work email or straight. With the popularity and its wide acceptance by security professionals it is not a surprise that even during the recent pandemic the stock price has been trough the roof rising with more than 50% for the last 2 months. [8]
SPLUNK
If there is one App in the Cybersecurity world that mirrors the impact of Microsoft Office had on business applications its name is SPLUNK. Splunk is a platform to search, gather, and analyse machine - generated date (aka logs) from servers, applications, and network devices. [9] It has the ability to work with large amount of data and is especially helpful in IR (Incident Response) because of the visibility in audit trails that provide. It has the capability to work with any logs that are in a syslog format, that's pretty much the whole IT infrastructure of a company.
The general wisdom is that SPLUNK is a security app, however this is not quite the case. It is widely used for business analytics derived from logs of Social Media applications including Facebook, Instagram, and Tinder. Like any modern application it comes out of the box with the functionalities like creating custom alerts, dashboards, and reports.
To anyone who wants to penetrate into the security profession! SPLUNK is a must. I would you are Baruch student in a Cybersecurity Major and are reading this article, the first thing to do while still in school is to familiarize with the application. As a heads up, on their website there is a free certificate that only take about 24 hours to complete but will provide a huge competitive advantage when you are looking to start your carrier.
Ring Inc.
Founded in 2012, Ring is the reinvention of the doorbell with a mission to reduce crimes in the neighborhood. It was created by Jamie Siminoff and a few college graduates in a garage in Southern California and was originally named Doorbot. Through crowdfunding, Doorbot raised $364,000, which is over a hundred thousand more than they had originally requested. [10] In 2013, DoorBot appeared on Shark Tank and left without any offers. Siminoff decided to rebrand the company to be called Ring and received over $5 million in sales. [11] On April 12th, 2018, Ring was acquired by Amazon. [12]
Ring plans on increasing home security with a wide range of products such as a video doorbell, security camera, smart lighting, security systems, as well as many other accessories. Ring products are based on a simple principle. By using your existing home Wi-Fi network, Ring products use the free Ring app to alert you whenever someone approaches your door or comes in a range of a security camera. You can then view an HD video stream of the person and speak to them using two-way audio communication. The free Ring app also allows you to control all the other functions of your Ring devices such as floodlights and sirens and video recording. The benefit of the app is that it allows you to always be home with a click of a button. [13]
Ring has also created a new community platform for neighbors to notify other users on any suspicious activity in the area or if there is a emergency in the area. Through the Neighbors App, it brings your community together and allows you to help create safer neighborhoods. With crime and safety alerts from your neighbors, law enforcement and the Ring team, the Neighbors App helps to keep you alerted in real-time. [14] Alerts can be about a house fire on a specific street or about a stolen package and specific details about what the suspect looks like.
The app relates to New Media because it is a technological advancement. The app has protected people from strangers at their door, local crimes and has allowed people to always be aware of what is happening in the area even if they are miles away from home. In 2010, Ring partnered with the Los Angeles Police Department and installed Ring Video Doorbells in 10 percent of homes in Wilshire Park, California. Data from the LAPD shows that there was a 55 percent decrease in break-ins within the first six months of the doorbells being installed. Ring has also helped police identify suspects through its video recording. [15]
References
- ↑ [3], https://en.wikipedia.org/wiki/Security.
- ↑ [4], https://www.cisco.com/c/en/us/products/security/firewalls/what-is-a-firewall.html.
- ↑ [5], https://us.norton.com/internetsecurity-malware-what-is-antivirus.html.
- ↑ [6], https://www.techworld.com/security/what-is-encryption-3659671/.
- ↑ [7], https://www.cisco.com/c/en/us/products/security/common-cyberattacks.html.
- ↑ https://www.dell.com/support/article/en-us/sln316407/what-is-crowdstrike?lang=en
- ↑ https://www.crowdstrike.com/
- ↑ https://www.google.com/search?q=crowdstrike+stock+price&rlz=1C1CHBF_enUS890US890&oq=Crowdstrike+&aqs=chrome.2.69i59j0l3j69i60l2j69i61j69i60.37997j0j7&sourceid=chrome&ie=UTF-8
- ↑ https://www.splunk.com/en_us/legal/splunk-software-support-policy.html
- ↑ https://web.archive.org/web/20130126033130/http://www.technewsdaily.com/16580-doorbot-homeowners-funding-goal.html
- ↑ https://www.businessinsider.com/ring-doorbot-shark-tank-goldman-sachs-2017-1
- ↑ https://blog.ring.com/2018/04/12/ring-now-part-amazon-family/
- ↑ https://ring.com/
- ↑ https://shop.ring.com/pages/neighbors
- ↑ https://www.abc15.com/news/national/technology-helping-to-deter-holiday-package-thieves