P2P Network
A peer-to-peer (P2P) network is a type of decentralized and distributed network architecture in which individual nodes in the network (called "peers").This network acts as both suppliers and consumers of resources, in contrast to the centralized client–server model where client nodes request access to resources provided by central servers.
In a peer-to-peer network, tasks (such as searching for files or streaming audio/video) are shared amongst multiple interconnected peers. Besides, peers can make a portion of their resources (such as processing power, disk storage, or network bandwidth) directly available to other network participants, without the need for centralized coordination by servers.
History
P2P systems had previously been used in many application domains, however the concept was popularized by file sharing systems such as the music-sharing application Napster (originally released in 1999). The peer-to-peer movement allowed millions of Internet users to connect “directly, forming groups and collaborating to become user-created search engines, virtual supercomputers, and filesystems.”
The idea of peer-to-peer began in the 1960s, when ARPANET was created as a network to share files between US research facilities and every host was seen as equal, none more important than the others.[1] As a precursor to the Internet, ARPANET was a successful client-server network where “every participating node could request and serve content.” However, ARPANET was not self-organized and it lacked the ability to “provide any means for context or content-based routing beyond ‘simple’ addressed based routing.”[1]
Therefore, a distributed messaging system that is often likened as an early peer-to-peer architecture was established: USENET. USENET was developed in 1979 and is a system that enforces a decentralized model of control. The basic model is a client-server model from the user or client perspective that offers a self-organizing approach to newsgroup servers. However, news servers communicate with one another as peers to propagate Usenet news articles over the entire group of network servers.
In May 1999, with millions more people on the Internet, Shawn Fenning introduced the music and file-sharing application called Napster.[1] Napster was the beginning of peer-to-peer networks, as we know them today, where “participating users establish a virtual network, entirely independent from the physical network, without having to obey any administrative authorities or restrictions.”[1]
P2P Applications
P2P, which can also be referred to as "peer-to-peer" is a web-based application that allows individuals to share, transfer and download files VIA the internet; P2P itself is internet technology. From Security and IT perspectives, P2P can be very evasive, prone to misuse, uses excessive bandwidth, and comes with various vulnerabilities such as spyware, malware, and threats. P2P technology as it is, can be very disruptive and there are several concerns whether or not it helps promulgate internet crimes such as privacy, infringement, and copyrights; as a matter of facts, P2P applications are closely monitored or denied on most network, be it a private/public company because of its characteristics.
File sharing is the sharing of computer data or space via public or private in a network with different levels of access. According to Techopedia, file sharing is the practice of sharing or offering access to digital information or resources, including documents, multimedia (audio/video), graphics, computer programs, images and e-books. It is the private or public distribution of data or resources in a network with different levels of sharing privileges. Sharing files in the physical world and outside a network is a very common and simple process, consisting of handing or mailing the files using a carrier. However, since the majority of everyday activities are shifted online, there was a need for an online file transferring software. And this is what file sharing offers. File sharing also allows multiple users to use the same file but making changes, editing, adding content, printing or simply reading it. In addition, it also means having files stored in a common file system, where other people also have access to. When a file can be shared it allows access to a specific number of users and with different levels of access. Also, with file sharing, there can be an allocated number of space in terms of storage. In addition, P2P file sharing allows users to gain access to certain files such as movies, music, and games. This type of sharing uses a P2P software that searches for other computers on a network. The Peers are end-user computer systems. One of the earliest examples of P2P sharing was nester and currently, torrent websites such as BitTorrent are other examples. In the article on wired.com titled "The BitTorrent Effect", "Bram Cohen is the creator of BitTorrent, one of the most successful peer-to-peer programs ever. BitTorrent lets users quickly upload and download enormous amounts of data, files that are hundreds or thousands of times bigger than a single MP3." Cohen noticed the problem with file sharing is that upload and download speeds aren't equal. Therefore, he realized that breaking the file up into pieces and the more popular the file is the faster the download speed. "Give and ye shall receive" became Cohen's motto.
File sharing can be private or public sharing of data or space in a network with various levels of access. Some examples of file sharing are Airdrop, google drive, dropbox, and Apple iCloud. Remember back in the days using LimeWire to download songs that you had to otherwise pay for? That is also file sharing! P2P or Peer to Peer file sharing is sharing digital media between two or more people using P2P networking technology. P2P file sharing allows users access to media files such as movies, games, music, and books. You don’t need fancy or expensive software programs for P2P file sharing and it is very convenient and fast. In the article “Peers Find Less Pressure Borrowing From Each Other” by Wendy Kaufman, one example of P2P is being discussed. Google teamed up and invested $125 million with Lending Club, which “gets borrowers and lenders together outside the conventional banking system.” People who needed a loan but didn’t want to pay high interest rates turned to Lending Club, which offered a much lower rate. They get lower rates because peer to peer lending operates like a marketplace. It is more direct and everything takes place through technology and the Internet to lower cost. I think P2P is beneficial for everyone, as long as it is convenient and legal. [2]
Pirate Bay
One of the biggest websites to obtain torrent files, Pirate Bay, has been through many conflicts with the law in the past but the lack of adaptation of the law to the growing pace of the digital age allows for the continual revival of the website. All three founders of the well known site have been arrested, two already fined millions of dollars and received prison time, the third being caught in Thailand, and will soon face prosecution. The website has faced many domain seizures, and shutdowns, eventually it was run off the web and no longer operational. It was one of the original P2P sharing websites, a pioneer that opened the concept of peer too peer sharing sites, but simply violated too many copyrights and other laws many of which were only formed after the site's creation. [1]
P2P Networks
According to Wikipedia, “file sharing is the practice of distributing files or providing access to digitally stored information, such as computer programs, documents or multimedia.” Whereas, P2P (peer-to-peer) file sharing is done with the help of downloading software such as Torrent, Kaaza and Lime Wire. Users use software to connect into the P2P network, where they find a vast variety of different files available for direct download from other users on the network. P2P software breaks large files into smaller portions, which is being uploaded from different servers and then reassembled/combined by the downloading software. Peer-to-peer file sharing is not limited to music sharing, but also e-books, movies, TV shows, software and much more. Nevertheless, I think the P2P file sharing will grow over the years because it is cheap and allows instance transferring of data.
Utorrent
There are certain websites that are completely free and one can upload as much as data as possible but the security and quality of the information are not monitored by the service providers that can put one’s system on the risk of getting affected by malware when visiting or sharing information on such websites. and torrents website are the main ones.
Utorrent (read 'micro torrent') is a lightweight client for tor networks. It provides protocol encryption in order to prevent ISP's from throttling or blocking traffic to the client. Protocol encryption changes the header of a packet sent to the random looking header with a payload so that it looks like regular transmissions, such as HTTP or FTP, therefore preventing traffic shaping and detection from ISP side. Utorrent supports Distributed Hash Tables, magnet links and tracker-less torrents. Utorrent allows for automatic port translation to a router so that no manual configuration is usually required (UPnP). It also features RSS downloading, SSL, Super Seeding mode, and a Boss key allowing hide the client from the view and the taskbar. [3] [4] [5]
BitComet
BitComet(Originally named SimpleBT client)is a P2P file sharing program that includes torrents. The program is written in C++ and is available for Microsoft Windows in 52 different languages[[2]]. The program allows simultaneous downloads, which means you can download as many files as you want. Files could include movies, music, games, applications, etc. BitComet features include an embedded Internet Explorer window inside BitComet, allowing the user to search for torrents to download. It also supports UPnP gateway configuration, bandwidth scheduling, web seeding(which is having files on your computer and letting others access it) and Nat traversal, which maintains internet protocol.
Vuze
Another popular P2P network is Vuze (formerly known as Azureus), which uses Java and Bit-Torrent clients to form software that users can download onto their computer devices. Once the software console is downloaded, users can search for thousands of downloadable items. Vuze prides itself on collecting a database of files from all other torrent and P2P networks so that users do not have to search more than one network. One benefit many users find when using Vuze over other Bit-torrent or P2P networks is that it offers anonymity to users. Another benefit that Vuze offers is that it allows users to convert the files they wish to download into any type of extension. For example, a movie that is uploaded by one user as a .avi can be downloaded by another as a .mp4 and watched on the Vuze software itself. Lastly, Vuze supports the following languages on its platform; Arabic, Brazilian Portuguese, Bulgarian, Catalan, Chinese (Simplified), Chinese (Traditional), Czech, Danish, Dutch, English, Finnish, French, Galician, German, Greek, Hebrew, Hungarian, Italian, Japanese, Korean, Lithuanian, Malay, Norwegian, Polish, Portuguese, Romanian, Russian, Spanish, Swedish, Thai, and Turkish. [6]
Businesses
P2P network is an application that can make a difference in the businesses. Many companies are using P2P network to make an efficient and useful system. It empowers consumers to have a great opportunity to trade each other efficiently. there are many market places that utilize P2P systems.
Commercial
eBay Inc. is an American multinational e-commerce corporation based in San Jose, California, that facilitates consumer-to-consumer and business-to-consumer sales through its website. The company manages the eBay website, an online auction and shopping website in which people and businesses buy and sell a wide variety of goods and services worldwide. The website is free to use for buyers, but sellers are charged fees for listing items after a limited number of free listings, and again when those items are sold. [7]
Car Sharing
Zip Car - People can be lent cars on the online and pick up the car offline. [8]
mission: to enable simple and responsible urban living [9]
Communication
Skype- Skype is well known for P2P using business. P2P system help Skype to maintain the centralized server and deliver voices to each other
Lending Club
Lending Club is one of U.S’s most popular peer to peer lending site. The lending club was founded in 2006 as one of Facebook’s applications. After gaining much popularity and receiving $10.26 million in funding it was developed into a full-scale peer to peer lending company by Norwest Venture Partners and Canaan Partners in August 2007. Lending Club was the first peer to peer lender to register its offerings as securities with the Securities and Exchange Commission (SEC). Lending Club is viewed as a pioneer in the fintech industry and was considered as the largest technology IOP of 2014 in the U.S.
Limewire
Limewire was a very popular free P2P network that was started around the year 2000. Similar to other P2P networks, Limewire ran on Java and used a Bit-Torrent Protocol. [11] Limewire offered users a free version of the software that was basic or an upgraded version of the software that offered faster search results and download times for a yearly fee. Although many users enjoyed this software for P2P sharing, users often unintentionally download a variety of different malware and viruses on their computer systems with downloads from Limewire. In addition, back in 2005, Limewire was being sued in court based on the allegation that it encouraged people to commit copyright infringement. As of 2010, Limewire had to shut down further upgrades and end further enhancements because of continuous legal woes. This was mainly because of suit filed against Limewire LLC by RIAA (Recording Industry Association of America) on behalf of eight major music publishers, claiming that Limewire actively allowed users to engage in music piracy, as most users of the software used it to download music for free that would have otherwise need to have been purchased. [12]
Limewire was great, but it did promote many computer viruses and encouraged copywriting. This was definitely a big change and led people to think that it was okay to copyright because it was that easy. Many artists were not happy at all, which is understandable. They stopped making money, because who is going to pay over one dollar for a song on iTunes when they can get many for free?
BitTorrent
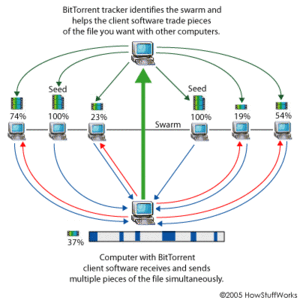
BitTorrent is a file distribution system used for transferring files across a network of people. As you download a file, BitTorrent places what you download on upload for other users; when multiple people are downloading the same file at the same time they upload pieces of the file to each other. BitTorrent pieces together the file you are downloading, to where the first part of a file you get may be the last part someone else gets. As you continue to retrieve the file, BitTorrent also uploads data to other users. For example, a person with 98 percent of the file done is directed to the people with the 2 percent of the file they still need. [13]
4shared is also a popular P2P website. On this website, the users are able to share their data, including music, video, photos and other types of files. The website was built in 2005. The website offers different language services, such as English, Chinese, Korean, French, Italian, Polish, and Japanese, etc. However, since the problem of copyright, the company now requires log-in from the users and became very limited. [14]
Data Streaming
Data streaming is sending a continuous flow of network packets over a medium such as Ethernet or Wifi. Data streaming is a popular method of transferring files across the internet mainly because it does not require central storage of data, instead, files are read on demand by remote computers., therefore increasing transmission speed. Services such as Netflix, HBO Go, Hulu or iTunes are using data streaming to deliver content to their clients. It's ease of implementation and low cost relative to other methods is the main driver for many companies for switching from traditional data delivery to data streaming. [15]
Data & Video streaming requires more bandwidth than usual. Internet providers are not happy about this and have been putting limits on customers' bandwidth which effects the performance of their services such as Netflix. According to an article by Jon Brodkin on 2/10/14, the Netflix service has been dropping for months on Verizon & Comcast internet services. [16]
Copyright Law
Copyright law was enacted to provide a safety net for the artists and their fixed and tangible work. While the use of the copyright notice is not required, it serves as an information source that indicated the protection of the work by copyright. The law is intended to protect intellectual property of the artists from being copied, being used to create another form of work that relies on the original work, distribution of copies to the public, staging the working by the means of a movie, theater or dance, and showing the property in public by the means of graphical or sculptural works.
The indication that the work has been published with the permission of the work owner is required on all publicly distributed copies of the work. Since the registration of the copyrights with the U.S. Copyright Office is not required, it does provide benefits of doing so. Benefits include an official establishment of the record of requesting copyright claims and registration is usually used as sufficient evidence of the validity of the copyright in court. [17]However, enforcing copyrights have been difficult due to digital file sharing through peer-to-peer (P2P) networks. Copyright law was put into effect in an era of server-based distribution rather than in an era such as now with P2P network distribution, hence copyright laws are put into question in regards to upholding the balance between copyright owners and the public domain.Copyright Issues in Digital Media
The relationship between the foundational moral philosophies and Copyright and Patent law
Copyright and patent law is primarily derived from utilitarian theory, because it gives power to a developer to have the ownership of his work, increase creativity and innovation, and encourage disclosure. It is illegal and harmful to copy private software in a society that grants the ownership of copyright or patent, because it deprives the owner of his legal right to require payment in exchange for the use of the software. Regardless of the utilitarian establishment of patent and copyright law, proprietary rights in software are sometimes supported as a count of natural right. According to natural right arguments, “since individual own themselves, they own their labor” (Johnson 124). This leads individual to have a right, which is natural right, to own whatever they produce with their labor. In addition, the natural right arguments are the essential idea of John Locke’s labor theory. He says, a person had the right to own his labor in a state of nature. For example, if one was to find an abandon place and use it to produce vegetable or for their own benefit, then this person have the ownership of what they produced. It will be wrong for someone else to take advantage of this person’s labor.
People can enslave an individual by acquiring the fruits of his labor, because an individual sovereignty and self- ownership and his labor are drawing out of his self (his body). Therefore, by owning the products of another individual’s labor, you make the person a slave. However, according to Nozick (1974), when an individual mixes his labor with something else it lessens the strength of natural right. Nozick is not against ownership of one’s self or one’s labor, rather she says, if you mix your labor with someone else’s property, you could lose a right in mixed product. For instance, it is clear that when you use free code, the free quality of the code contaminates whatever other codes it touches. Therefore, by mixing free code with your labor, you cannot claim to have the ownership of your labor because it violate and goes against natural right claims. As a result, intellectual property rights are not natural but a matter of social utility.
Fair use and the public domain is related to the moral philosophy that copyright and patent largely derive from utilitarian theory. Since the theory is based on creating good consequences which is an amount of happiness for others. In addition, fair use allows people to create good consequence in the society by using copyright and patent for the purpose of critic, comment, news reporting, teaching, scholarship or research.
The act of DIP piracy (illegal copying) is extrinsically immoral because copying the work of somebody else does not make you take his/her work from him. The person will continue to have his intellectual property. For example, when an intellectual product such as musical tunes or ideas has been copied, the owner does not lose ability to the product of his work. However, the act of copying an individual labor will prevent him to make money from his own work. Hence, this is why software developers want to have a right to control their software for economic gain in a market environment.
The moral philosophy that copyright and patent largely derive from is the regulation in which specify what an individual can and cannot own, how things may be acquired and transferred, and what an individual can do with his/her property. In addition, the government can confiscate your ownership whenever they want.
The Four Factors of Fair Use
There are four factors of fair use. According to Richard Stim [18], the first factor is: The Purpose and Character of Your Use. The court will examine if the material taken from the original work has been transformed by the means of new expression. Did the individual add new meaning to the work? Did they add value to the original work by adding new information and understanding based on their own findings? The second factor is: The Nature of the Copyrighted Work, which gives the user of the copyright more freedom when copying factual works, since facts cannot be copyrighted. Copying work from an unpublished author bares more consequence because the author of the work has the right to control when their work of expression becomes public, or if their work ever becomes public. The third factor is: The Amount and Substantiality of the Portion Taken. The less information you take from the copyrighted source, the more likely you are to be excused on the basis of fair use. However, if the user copies a small but, major part of the work, this could be problematic. For example, copying a very important line from a song and using that one line will not constitute as fair use. Another case in which this rule is not likely to work is the case of parody, in which the user can copy a chunk of the work, including the important parts to deliver their point. The fourth factor is: The Effect of the Use Upon the Potential Market, which focuses on depriving the owner to the economic benefits of their work. The use of a copiers work does not have to directly mimic the original work. For example, an artist decided to make a wooden sculpture of a photograph by another artist, selling the sculptures and profiting. This is important to know because in the digital world it is very easy to miscommunicate and diminish someone’s work without their permission. By remaining aware of the law and fair use, individuals are equipped with way to fight infringement of their intellectual property or ways to prevent themselves from being a suspect of infringement.
A very prominent issue is with social media platforms such as YouTube, where individuals merely state that the stuff in their video is not theirs. This does not provide much protection for the user of the content because they are admitting to improperly using the content without formally giving credit in properly formatted statements.
Bitcoin
Bitcoin is what is known as a digital currency; a medium of exchange that is purely made of computer bits and data. In other words its a type of money that can be used to purchase things. However, the way it operates is opposite to how our bank issued bank notes operate. This is because bank issued-currency and even credit cards from credit card companies operate in a centralized manner, whereas Bitcoin is a decentralized currency that is basically managed by the participants in the global digital economy.Essentially, Bitcoin is a P2P program where every user participates in its distribution and maintenance.
What exactly do the terms decentralized and centralized in this context mean? A centralized currency is a currency that is monitored and managed by one main entity such as a bank or a credit card company. For example, the banks determine the value of our money and act as a third party intermediary during transactions. In other words, an entity such as a credit card company would keep record of every user and be in charge of transferring money from one account to another during a transaction. This was done for many years before the introduction of bitcoin as a solution to a problem known as the "double spending problem". This occurred when one would transfer money from one account to another, the money essentially acted as a file document being copied from one computer to another. When this happens, the file stays on the original computer after a copy has been made. Thus, essentially two copies were made and entities such as credit card companies were in charge of managing this problem.[19]
Bitcoin relies on all of its participants to determine its value through the laws of supply and demand. Furthermore, every participant on the Bitcoin economy is responsible for monitoring the transactions that take place. This is done through a public record or "block chain" that is monitored by special programmers known as "Miners". They are called miners because they oversee the Bitcoin creation process which is said to have been designed to emulate the way gold is mined in real life. According to the miners' calculations, the last bitcoin will be "mined" in 2140. The main technology behind Bitcoin is cryptography, which involves using a public key and a private key. Public key can be seen by everyone on the network, which the miners use to verify it as a legitimate transaction of bitcoins. The private key is similar to a password and is used to verify that the initiator used it to sign the public key, in order to determine that the intended recipient is now the new owner of the funds.[20]
Bitcoin's advantages include no extra fees since there is no third party intermediary such as a credit company to charge for their services. This makes it very enticing small businesses for all their needs when performing various types of transactions. Bitcoin transactions are also irreversible, which helps businesses fight a problem known as charge-backs. This involves customers claiming they did not receive a product, causing the business to reverse the transaction and return the money to the customer. This is problematic because the business does not earn any revenue and loses the product as well. [21]
Video Games
Some Video Games rely on a P2P connection between the host and other users. It is a low-cost method of online gameplay as it relies only on creating a connection between players and not running servers which can be high maintenance. Among most gamers, P2P is usually viewed negatively as it can cause a lot of unfair advantages to the host and problems for other users. Some of the other drawbacks to players include input lag, connection issues (or drops when the host leaves the game), and a hard time finding an online game as it sometimes will require the user to setup their Internet connection to allow specific P2P settings. Privacy concerns also exist with P2P video games as any peer in the connection is able to track the users' location with the proper equipment. The most notable use of P2P in recent years is the free-to-play MMORPG SKYFORGE. At launch, SKYFORGE players criticized their launcher because it caused high latency issues and capped bandwidth. The client would begin seeding the game to other players without the consent of the user and would even perform background tasks without the users' knowledge. This incident highlighted the double-edged problems that may arise in P2P sharing. [22]
Structure
Unstructured networks
Peer-to-peer architecture (P2P architecture) is a commonly used computer networking architecture in which each workstation has the same capabilities and responsibilities. Each node in the network plays the role of a server and a client simultaneously. The most common application that P2P networks have is content distribution. Streaming media, peercasting[23] and software distribution. There are 2 models of unstructured P2P computer network architecture: Pure P2P, Hybrid P2P, and Centralized P2P.
Gnutella[24] is a file sharing protocol decentralized P2P networks removing the single point of failure of centralized maintenance servers. The concept was to design a highly available network that contributes to the major design goals of peer-to-peer file sharing systems[25].
Structured networks
Security issues
Using a P2P software or program could potentially affect you. First, you could download a file which is actually a virus. Second, by having a torrent and files on your computer, you're allowing other people to download the same file to their computer, using your connection. Third, if you're sharing an illegal file(such as movies,music, games) you can get sued because you're breaking copyright laws.
Data backup, recovery, and availability
Growth
P2P file sharing continues to grow more and more popular each day. One major step in the growth of P2P sharing was Google's decision to team up with the nation's largest peer-to-peer lender. Google's actions resulted in a growing interest of P2P file sharing. Wendy Kaufman's article "Peers Find Less Pressure Borrowing From Each Other" gives the audience a great insight on how P2P file sharing can serve as a lot more than just a place to share music, movies, and games. It can also be used as a platform for peer-to-peer lending operations where funding can be a lot easier for investors and borrowers. [26]
Resource sharing
Anonymity
Network neutrality
Net neutrality refers to Internet service providers and governments viewing all data equally. Rather than discriminating user by user, it wants all data to have the same value[27]. The origins of this term came from Tim Wu, a Media Law Professor in Columbia University in 2003[28].
The data that net neutrality is aimed at includes all types of messages, files, and data that is shared over the Internet. This includes emails, audio files, video files and more.
References
Deborah G. Johnson, and Keith W. Miller. Computer Ethics: Analyzing Information Technology. Pearson Education International, 2008.
- ↑ 1.0 1.1 1.2 1.3 Steinmetz, R., & Wehrle, K. (2005). 2. What Is This “Peer-to-Peer” About? (pp. 9-16). Springer Berlin Heidelberg.
- ↑ https://www.wnyc.org/story/292453-peers-find-less-pressure-borrowing-from-each-other/
- ↑ http://wiki.vuze.com/w/Message_Stream_Encryption
- ↑ http://en.wikipedia.org/wiki/Distributed_hash_table
- ↑ http://www.utorrent.com/help/faq/misc#faq3
- ↑ http://download.cnet.com/Vuze/3000-2196_4-10295479.html
- ↑ https://www.ebay.com.au/help/selling/fees-credits-invoices/fees-credits-invoices?id=4070
- ↑ https://www.currencyfair.com/blog/peer-to-peer-marketplace-revolution-50-companies-changing-world/
- ↑ https://www.zipcar.co.uk/mission
- ↑ https://www.lifewire.com/skype-changes-from-p2p-3426522
- ↑ https://en.wikipedia.org/wiki/LimeWire
- ↑ http://www.pcworld.com/article/208895/Limewire_Shut_Down_Permanently.html
- ↑ www.webopedia.com/TERM/B/BitTorrent.html
- ↑ https://www.4shared.com/
- ↑ http://en.wikipedia.org/wiki/Data_stream
- ↑ http://arstechnica.com/information-technology/2014/02/netflix-performance-on-verizon-and-comcast-has-been-dropping-for-months/
- ↑ “A Very Brief Summary of Copyright Law”, Axley, 1 October 2008. Retrieved on 29 June 2014.
- ↑ https://fairuse.stanford.edu/overview/fair-use/four-factors/
- ↑ http://www.fincen.gov/statutes_regs/guidance/html/FIN-2013-G001.html
- ↑ http://www.fincen.gov/statutes_regs/guidance/html/FIN-2013-G001.html
- ↑ [3]19 Aug. 2013
- ↑ https://www.reddit.com/r/Games/comments/3ds68c/newly_released_mmo_skyforges_launcher_is_a_p2p/ct8e6o6/?context=3
- ↑ http://en.wikipedia.org/wiki/Peercasting
- ↑ http://ra.crema.unimi.it/turing/materiale/admin/corsi/sistemi/lezioni/m3/m3_u2_def/ceravolo_file2.pdf
- ↑ http://ra.crema.unimi.it/turing/materiale/admin/corsi/sistemi/lezioni/m3/m3_u2_def/ceravolo_file2.pdf/ Gnutella 0.6 Page 1
- ↑ http://www.npr.org/sections/alltechconsidered/2013/05/10/182651552/peers-find-less-pressure-borrowing-from-each-other
- ↑ https://www.nytimes.com/2017/03/30/technology/net-neutrality.html
- ↑ http://www.jthtl.org/content/articles/V2I1/JTHTLv2i1_Wu.PDF